Cyberattack: Ransomware-as-a-Service
Japan’s Asahi Group suffered a major ransomware attack by the Russian gang Qilin. Learn how Ransomware-as-a-Service (RaaS) works, its operational, financial, and reputational impacts, and the global cybersecurity implications.
Context:
Asahi Group Holdings, Japan’s leading beverage giant, was forced to halt production and saw its distribution networks crippled by a sophisticated ransomware attack by a Russian cybercriminal gang, Qilin. The gang operates on a Ransomware-as-a-Service (RaaS) model, and has been linked to over 870 attacks since 2022, including a significant breach of UK’s Synnovis that impacted hospital services.
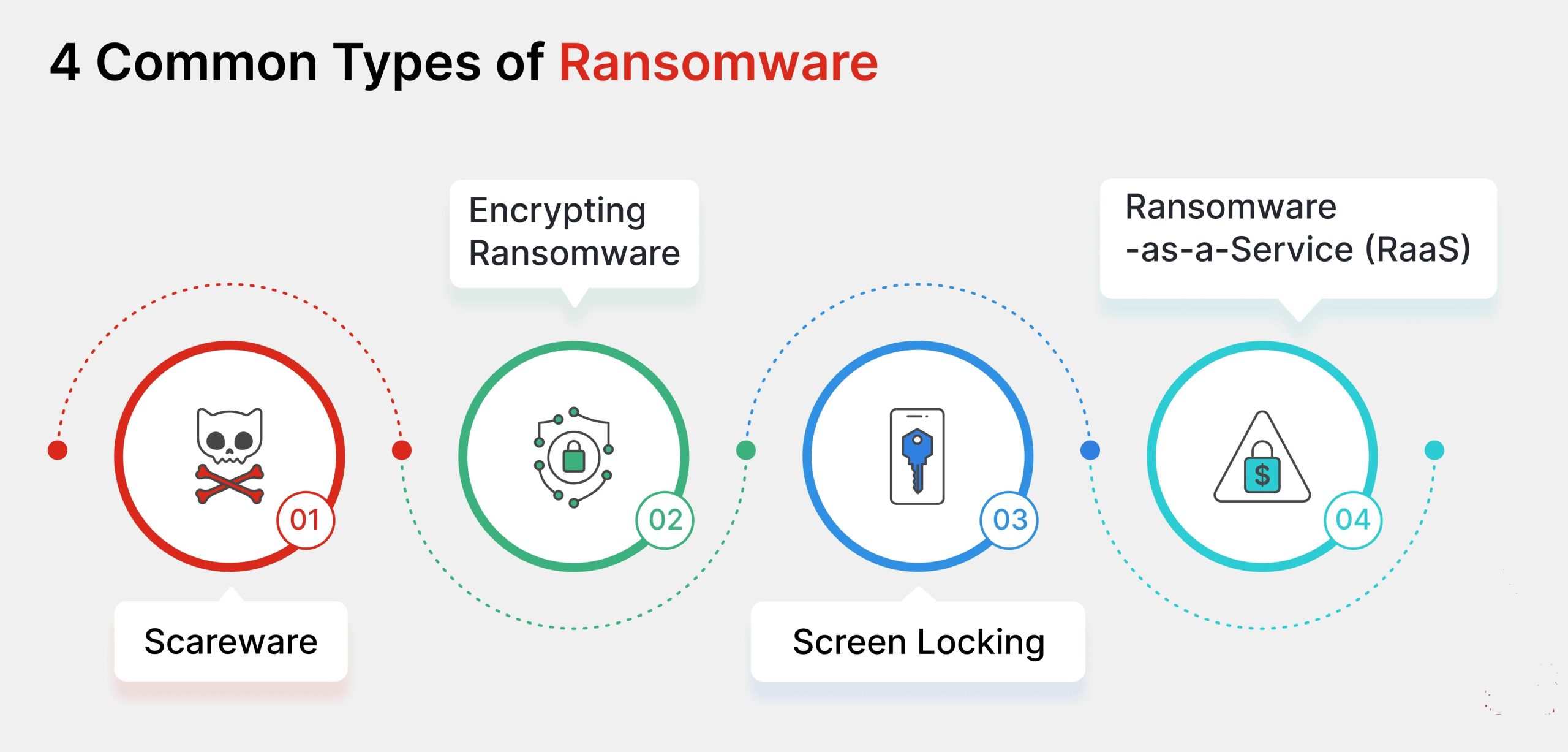
What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) is a cybercrime business model that mirrors legitimate software-as-a-service (SaaS) platforms. It lowers the barrier to entry for cybercrime by allowing technically unskilled individuals (“affiliates”) to launch sophisticated ransomware attacks.
- How it Works: RaaS operators (like Qilin) develop and maintain the ransomware toolkit—the malicious software, the payment portals, and the support infrastructure. They then lease or license this “service” to affiliates on the dark web.
- Revenue Model: In exchange for providing the tools and platform, the RaaS operators take a cut of the ransom payments, typically 20-30%. The affiliates carry out the actual attacks and keep the majority of the extorted funds.
- Example: The Qilin Model: Qilin is a prime example of a RaaS provider. They:
- Provide malware written in Rust and C, capable of targeting Windows, Linux, and ESXi systems.
- Set the rules of engagement for their affiliates (e.g., prohibiting attacks on Russia and Belarus).
- Manage the leak sites where stolen data is published to pressure victims.
- Earn a commission from every successful ransom paid to an affiliate using their platform. This model has enabled Qilin to become one of the most active ransomware gangs in 2024.
What are the multidimensional impacts of such Cyber Attacks?
The impact of a major ransomware attack like the one on Asahi extends far beyond a temporary IT outage, creating a ripple effect across multiple dimensions.
-
Impact on the Service Provider/Company:
-
-
- Operational Disruption: As seen with Asahi, production can be completely halted, and supply chains disrupted, leading to significant revenue loss.
- Financial Loss: Costs include ransom payments (if made), costs for incident response and system restoration, and a decline in stock value.
- Reputational Damage: Loss of customer and partner trust can have long-term consequences, especially if sensitive data is leaked.
- Legal and Compliance Risks: Companies may face lawsuits from affected parties and penalties for failing to protect data under privacy laws like GDPR or India’s DPDP Act.
-
-
Impact on Consumers and the Public:
-
-
- Product Shortages: Halts in production and distribution can lead to shortages of essential goods, from medical supplies (as in the Synnovis case) to consumer products like beer, affecting availability and price.
- Compromised Personal Data: If customer data is stolen, it can lead to identity theft, financial fraud, and a loss of privacy.
- Erosion of Trust in Digital Services: Repeated attacks undermine public confidence in digital transactions and the ability of institutions to protect their information.
-
-
Impact on the Economy and National Security:
-
- Macroeconomic Damage: Widespread cyberattacks on manufacturers and critical industries can disrupt national supply chains, reduce GDP, and create economic instability.
- Threat to Critical Infrastructure: When attacks target healthcare, energy, or food and beverage sectors, they blur the line between criminal activity and a threat to national security and public safety.
- Innovation Drain: Resources that could be spent on research and development are diverted to cybersecurity and damage control, stifling innovation.
The United Nations Convention against Cybercrime, 2024 (UNGA) and Budapest Convention on Cybercrime, 2001 (Council of Europe) aiming to strengthen international cooperation and create a global framework to combat cybercrime and protect against digital threats are steps in the right direction.
Subscribe to our Youtube Channel for more Valuable Content – TheStudyias
Download the App to Subscribe to our Courses – Thestudyias
The Source’s Authority and Ownership of the Article is Claimed By THE STUDY IAS BY MANIKANT SINGH




